How Tor Works
Information Security Consultant @ Blit-Tech
Software Developer @ Shelter Insurance
Email: nabil@blit.tech
Agenda
- What Does Tor Do?
- How Does it do it?
- How is the Model Broken?
What is Tor?
The Onion Router
Connect to an endpoint through a series of Relays instead of making a direct connection
Uses
- Anonymity
- Censorship Resistance
- Hidden Service
Tor's Components
- Onion Proxy (OP)
- SOCKS Proxy into the Tor network
- Relay
- A node in the Tor network, sometimes called an Onion Router (OR)
- Exit Node
- The last node before the traffic exits the network
The Tor Network
Creating a Circuit
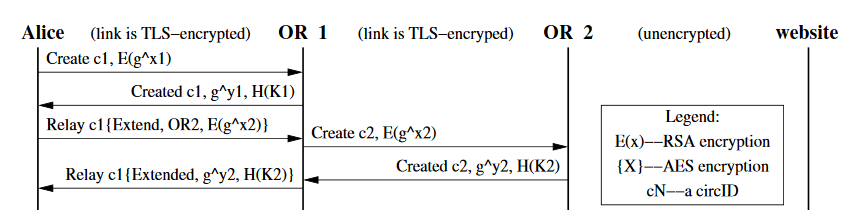
The OP Creates Circuits by extending them incrementally
Each node on the circuit only knows about the node proceeding it
Relaying Data
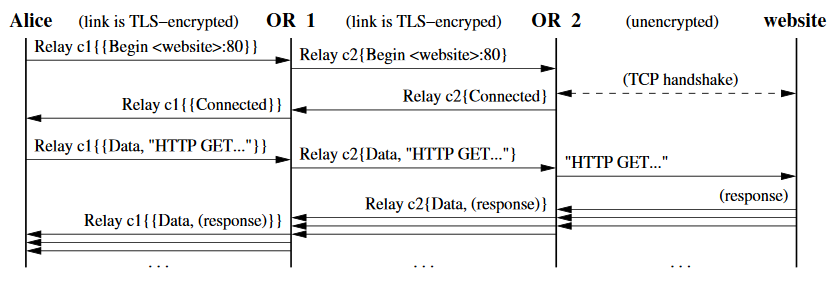
The OP recursively encrypts the data with the key for each OR in the circuit
Each OR decrypts the payload using it's key and forwards on to the next hop
Hidden Services
The Players
Bob The Hidden Service
Alice Wants to connect to Bob's service
Step 1: Introduction Points
Bob has a long-term asymmetric keys to identify his service
Bob chooses introduction points, creates a circuit to them and gives them his public key
Bob publishes the list of introduction points
Step 2: Alice wants to Talk to Bob
Alice learns Bob's public key out-of-band.
Alice chooses a rendezvous point (RP) and builds a circuit to the RP
Alice gives the RP a rendezvous cookie to recognize Bob
Alice builds a circuit to one of Bob's introduction points and tells Bob about the RP
Step 3: Bob connects to Alice's rendezvous point
Bob builds a circuits to the RP, and provides it with the connection cookie
The RP connects Bob's circuit to Alice's
Alice and Bob can communicate
De-anonymizing Tor Users
Protocol Leaking the IP
BitTorrent. Also, some VOIP Protocols do this too for NAT traversal
Cookies, browser fingerprinting etc
Advances techniques: Mouse movement fingerprinting, typing patters.
Flash, JavaScript, WebRTC (ICE) and DNS Queries
Bad OPSEC
There is no technical solution for this
Browser Exploits
FBI calls them NITs
Expensive, usually used to mass-unmask the users of a website
Traffic Analysis/Tagging
Theoretical and expensive but we've seen evidence of them being used