WiFi Insecurity
A tour of common attacks on WiFi networks
Information Security Consultant @ Blit-Tech
Software Developer @ Shelter Insurance
Email: nabil@blit.tech
What we are doing
Over of WiFi security standards and issues
Krack a network and read packets
No Physical Access Control
Maybe the only issue that is fundamental to wireless security
Most attacks use this to their advantage
WEP
Don't use this!!
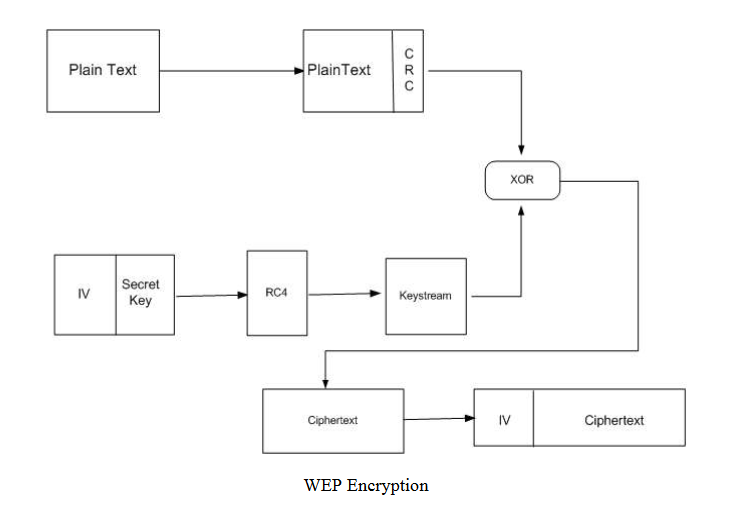
src: http://www.cs.sjsu.edu/~stamp/CS265/projects/Spr05/papers/WEP.pdf
The Core Problem is IV is used incorrectly
Key Reuse with RC4
WPA
Wi-Fi Protected Access
WPA Modes
- WPA-Personal: Static pre-shared key (aka. password). Most common in homes and coffee shops.
- WPA-Enterprise: Requires and authentication server, has lots of modes.
- WPS: Wi-Fi Protected Setup. Uses and 8-digit PIN. Broken, disable if you can.
WPA's Keys
- PMK: Pairwise Master Key, derived from the password (WPA-Personal) or the EAP parameters.
- PTK: Pairwise Transient Key,
PMK || ANonce || SNonce || AP MAC || Station MAC, used to encrypt traffic - GTK: Group Temporal Key, used to encrypt/decrypt broadcast traffic. Generated by the AP
The WPA Handshake
- The AP sends a nonce
ANonceand a Key Replay Counter to the station. - The station constructs the
PTK. The station sends a nonceSNonce, a MIC and the Key Replay Counter to the AP. - The AP verifies message 2 and then sends the
GTKand another MIC to the station. - The station verifies the AP's message and sends a confirmation
WPA 3
The Future!
Thank you Mathy Vanhoef
More Secure Handshake
Eliminates offline dictionary attacks and provides forward secrecy using SAE
Replace WPS
A little complicated, but is based on the devices wanting to connect providing a public key to the router
Unauthenticated Encryption
Not sure how this will work, but Opportunistic Wireless Encryption (OWE) is a strong candidate
What wasn't discussed
- KRACK
- WPS Pin Brute forcing
- TKIP Weaknesses
- Captive Portals
- Router-specific issues
- Lesser known issues
- "Regular" network attacks